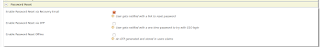
Maintain the history of the user’s passwords in Wso2 Identity Server 5.3.0
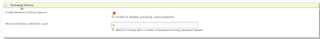
By using this feature it can keep the history of a user's past passwords according to a pre-configured count. This enables you to prevent a user from using a password he/she has used in the recent past. Detailed Instructions Login to the management console. 1. Click Resident under Identity Providers in the Main tab of the management console. 2. Expand the Password Policies tab. 3. Expand the Password History tab and select Enable Password History Feature. 4.Specify the Password History Validation Count and click Update. Expected Outcome If the user is trying to reuse his recently changed (according to the configurations) password as the current password it will give below error.