Secure Wso2 ESB REST APIs using Kerberos
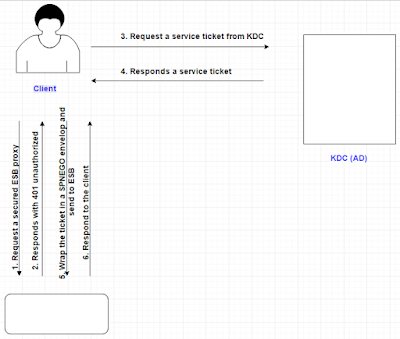
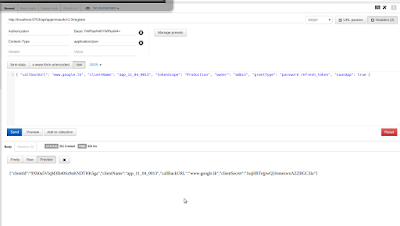
When a consumer attempts to consume a REST API, if the API is secured using some authentication protocol (e.g Basic , Kerberos, NTLM) the consumer has to prove his authentication to the API by sending credentials or relevant token through authorization headers. By default ESB REST APIs does not include any security and from this blog post I will speak about how to make the APIs secured using kerberos. I have used main 3 components ; Active Directory as the KDC , ESB server as the resource server and a C#.net client to invoke the rest APIs in ESB server. The design of the implementation is as below. The Design of the Kerberos Communication 1. Client tries to invoke the ESB proxy 2. The server responds with 401 unauthorized 3. Client requests a kerberos service ticket from active directory 4. If user is identified by the KDC (AD) it will send the SGT to the client 5. Client wraps the SPENEGO token in the request HTTP header and resend to ESB 6. ESB sees the HTTP header w